Pentest report
A penetration test was conducted to identify vulnerabilities in the company's internal network and exposed services.
The name of the was changed to ABC for confidential purposes
Executive Summary
This report summarizes the vulnerabilities and findings discovered during the pentest conducted on ABC in June 2023. The test was carried out by a group of masters students, who also have a keen interest in cybersecurity.
There are three phases in this penetration test (pentest). The first phase is the footprinting process, which involves gathering initial information about the target. The second phase entails identifying and collecting vulnerabilities present on the website. Finally, the third phase involves analyzing the internal network to uncover any potential vulnerabilities.
Objectives:
- Identify and assess potential security weaknesses in the target system or network.
- Determine an attacker’s ability to gain unauthorized access to sensitive data or confidential systems.
- Test the effectiveness of existing security controls and defenses.
- Assess the level of risk associated with identified vulnerabilities and recommend strategies to mitigate those risks.
- Test the security of third-party systems or services that are integrated into the target system.
- Verify the correct configuration of security devices, such as firewalls, intrusion detection/prevention systems, and VPNs.
Validate the security of Web applications.
Introduction
This document presents the findings and recommendations resulting from a comprehensive penetration testing conducted on the network and systems of ABC as part of a class project. The purpose of this assessment was to simulate real-world attack scenarios and evaluate the security posture of ABC’s infrastructure. By identifying vulnerabilities and weaknesses, this penetration testing aimed to provide valuable insights and recommendations to ABC, enabling them to improve their security measures in a controlled and educational environment.
As part of the class project, ABC agreed to participate in a simulated penetration testing exercise to enhance their understanding of cybersecurity risks and defenses and hopefully improve it. The objective was to apply theoretical knowledge gained during the course and gain hands-on experience in assessing and mitigating vulnerabilities. This penetration testing aimed to contribute to our educational development while providing ABC with valuable insights into their security posture, being advantageous for both ends.
The primary objectives of the penetration testing were to:
-
Identify vulnerabilities within ABC’s network infrastructure, systems, and applications.
- Evaluate the effectiveness of existing security controls and configurations.
- Assess the potential impact of successful attacks on ABC’s assets and sensitive information.
- Provide recommendations for remediation and best practices to strengthen ABC’s security defenses.
Our engagement was focused on assessing the security of ABC’s network infrastructure. The evaluation also encompassed web applications and associated components. It is important to note that this penetration testing exercise was conducted with the consent and collaboration of ABC, within the agreed scope and time, to facilitate a controlled learning experience and avoid unforeseen events.
The penetration testing followed a structured methodology, combining theoretical knowledge and practical techniques gathered from our theoretical and practical classes. The methodology included:
- Foot Printing : Gathering information about ABC’s infrastructure and potential attack vectors.
- Vulnerability scanning : Identifying known vulnerabilities through automated scanning tools.
- Exploitation : Attempting to exploit identified vulnerabilities to gain unauthorized access or elevate privileges.
- Post-exploitation : Assessing the extent of compromise and exploring potential lateral movement within the network.
- Reporting : Documenting the findings, including identified vulnerabilities, their potential impact, and recommendations for remediation.
This report, as stated above, presents the findings of the penetration testing exercise conducted as part of the class project. The subsequent sections will outline the identified vulnerabilities, categorized by severity levels, and provide corresponding recommendations for remediation. It is important to note that the recommendations are information restricted and focused on educational purposes, meaning that they may not fully capture the real-world complexities or specific requirements of a production environment required by the company.
In conclusion, this penetration testing exercise provided valuable insights into the security posture of J. Sousa’s network infrastructure and applications. The findings and recommendations presented in this report are intended to serve as an educational resource to enhance the understanding of cybersecurity risks and foster proactive security practices. ABC is encouraged to further explore and implement appropriate security measures to protect their systems and sensitive information.
Disclaimer:
It is crucial to acknowledge that this penetration testing exercise was conducted within an academic environment with limited scope and resources. The findings and recommendations presented in this report should not be solely relied upon for security decisions. ABC is advised to engage professional cybersecurity experts to perform thorough, and comprehensive assessments tailored to their specific requirements and operational environment.
Testing Environment
The Footprinting phase of the testing was meticulously conducted in a controlled environment using our own computers. We employed advanced footprinting tools and conducted extensive research on publicly available online databases to gather comprehensive information about the company, without any intrusion or unauthorized access to the target company’s systems.
For the network test, which encompassed scanning and sniffing activities, we established remote access to a designated computer within the ABC Wi-Fi network. Prior to conducting these tests, we obtained authorized access to the network, enabling us to securely connect and remotely control the machine. In this machine we installed a remote desktop application software that allowed us to be “inside” the company without being geographically restricted.
To assess the security of the website, we employed a diverse range of exploit techniques, ensuring a comprehensive testing and analysis process. This approach allowed us to thoroughly evaluate potential vulnerabilities and identify any areas of concern.
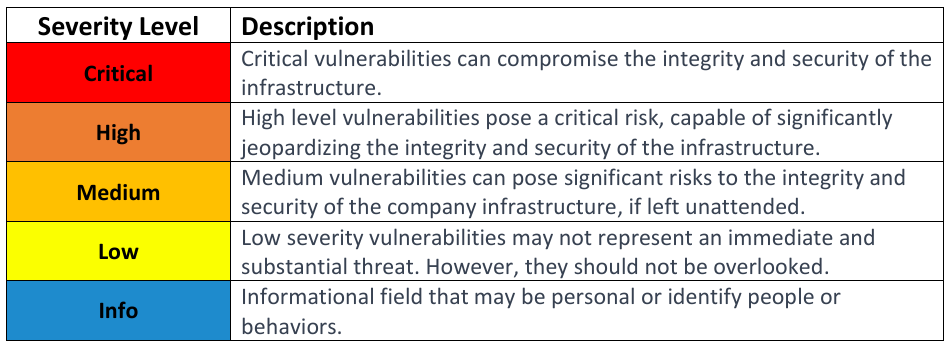
Each finding will be categorized based on their severity, allowing for a clear leveling and a fast prioritization of severe identified issues. The next table shows the three classification types and a brief description of their meaning.
FootPrinting
The footprinting process played a pivotal role in conducting a comprehensive investigation by meticulously gathering and assimilating an extensive array of online information related to the company and its associated domain. To achieve this, we employed various effective footprinting techniques and seamlessly combined them for a thorough analysis.
Through passive footprinting, we leveraged public sources such as search engines, social media platforms, and online directories, which allowed us to collect domain specifics, email addresses, employee names, IP addresses, and other relevant details. This initial step provided a foundation of knowledge about the company’s online presence.
Additionally, we utilized WHOIS lookup tools to obtain registration information for the company’s domain name. This process revealed crucial details, including the domain registrar, registration dates, and contact information, providing insights into the administrative aspects of the company’s online assets.
Furthermore, DNS enumeration techniques were employed to systematically query DNS servers and extract valuable information about the company’s DNS records. This enabled us to identify subdomains, mail servers, and associated hosts, further enhancing our understanding of the company’s digital infrastructure.
Email harvesting played a significant role in our investigation as well. By using specialized techniques and tools, we gathered email addresses associated with the company from publicly available sources such as websites, forums, and online platforms. This step allowed us to uncover valuable communication channels and potential points of vulnerability. However, due to time constraints, we were unable to employ social engineering techniques using the gathered information.
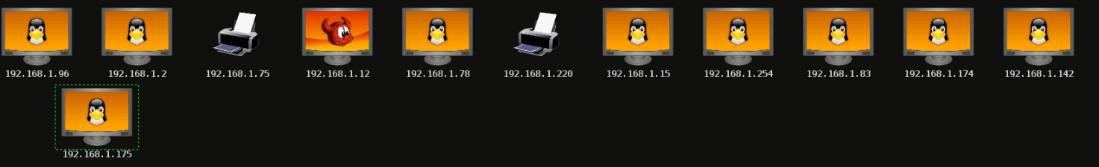
Lastly, we conducted network mapping to analyze publicly accessible networks and identify IP addresses associated with the company. This process provided insights into the company’s network topology, potential entry points, and critical infrastructure exposure, completing our comprehensive footprinting assessment. By seamlessly integrating these various footprinting techniques, we were able to gather a wide range of information about ABC. This comprehensive approach enabled us to identify potential vulnerabilities, assess the exposure of critical assets, and provide valuable insights to enhance the overall assessment of ABC’s security posture.
Findings
In the process of footprinting, we conducted a thorough search of emails associated with the ABC.pt domain. Our investigation revealed that a number of these emails have been compromised by platforms like luminPDF. To ensure the safety of your accounts, we highly recommend taking immediate action by changing your passwords and enhancing security measures for the following emails:
1
2
3
4
Services
ABC.pt
ftp.ABC.pt
clientes.ABC.pt
In order to obtain information about domain names and IP addresses we used the “whois” command. It is possible to access valuable details regarding domain ownership, administrative contacts, and other relevant information by executing the command followed by the domain name (such as “ABC.pt”) or an IP address. One key piece of information that the “whois” command provides is the name servers associated with the domain. These name servers act as the authoritative DNS servers responsible for handling DNS queries and directing traffic for the domain. By examining the name servers, you can gain insights into the infrastructure supporting the domain and further understand its technical configuration.
In our specific case, a significant discovery is that DreamHost provides all the name servers associated with the domain. This finding holds paramount importance as it reveals a crucial aspect of the domain’s infrastructure. The domain owner has entrusted their DNS management to a reputable and specialized service by relying on a server provider. DreamHost is a web hosting company that provides numerous services to individuals and businesses. It offers shared hosting, virtual private servers (VPS), dedicated servers, and cloud hosting solutions. It also provides domain registration services and has its own domain registration platform. DreamHost brings several advantages, like redundancy and load distribution since the domain has multiple name servers. By doing so, it helps to ensure the availability and reliability of the domain’s DNS resolution.
1
2
3
4
Name Servers
ns1.dreamhost.com IPv4 and IPv
ns2.dreamhost.com IPv4 and IPv
ns3.dreamhost.com IPv4 and IPv
Since the website’s name server and hosting are handled by a reputable and well-known company like DreamHost, we attempted to conduct further footprinting to uncover additional relevant information. Regrettably, our efforts did not yield any significant findings beyond this point.
The fact that the website relies on the services of DreamHost for both name server management and hosting signifies a deliberate choice made by the website owner. DreamHost’s established reputation in the industry suggests that the website benefits from reliable infrastructure and robust hosting solutions.
Despite our endeavor to gather more insights, it appears that the available information already highlights the key association with DreamHost. It is plausible that the website owner has taken measures to maintain privacy and limit publicly accessible details regarding their hosting configuration.
While we may not have uncovered additional noteworthy information, the reliance on a reputable hosting provider like DreamHost speaks to the website owner’s commitment to quality services and reliable infrastructure.
| Services | Emails |
|---|---|
| ABC.pt | x@ABC.pt |
| ftp.ABC.pt | x@ABC.pt |
| ABC.ABC.pt | x@ABC.pt |
ABC.pt Website Analysis
Performing a comprehensive website analysis involves employing a combination of automated tools and conducting a manual investigation to identify potential vulnerabilities. Among the numerous vulnerabilities that can pose a significant threat, SQL injection stands out as particularly perilous since it can grant unauthorized remote access to the entire database, leading to severe consequences.
Findings
| Severity | Name |
|---|---|
| MEDIUM | Content Security Policy (CSP) Header Not Set |
Content Security Policy serves as an additional security layer designed to detect and counteract specific types of attacks, such as Cross Site Scripting (XSS) and data injection attacks. These malicious activities range from unauthorized data theft and site defacement to the distribution of malware.
To combat these threats, CSP offers a set of standard HTTP headers that enable website owners to specify authorized sources of content that browsers should be permitted to load on a given page. These approved content sources encompass several types, including JavaScript, CSS, HTML frames, fonts, images, and embeddable objects like Java applets, ActiveX, audio, and video files. By employing CSP, website owners can exert greater control over the loading of external resources and mitigate potential security risks. To address this vulnerability, the company must include the Content-Security-Policy header in the requests of the webserver.
| Severity | Name |
|---|---|
| MEDIUM | Missing Anti-clickjacking Header |
Missing Anti-clickjacking Header refers to the absence of specific HTTP headers that protect web applications against Clickjacking attacks. Clickjacking is a technique where attackers deceive users into unknowingly interacting with malicious elements on a web page. The Content-Security-Policy (CSP) header with the ‘frame-ancestors’ directive or the X-Frame-Options header can mitigate these attacks. The absence of these headers exposes the application to Clickjacking vulnerabilities, enabling unauthorized actions or data disclosure. It is crucial to include these headers to ensure robust protection against Clickjacking threats.
Content-Security-Policy and X-Frame-Options HTTP are essential headers that improve the security of a web application. If it is possible to anticipate that a certain page will only be framed by specific pages on a server (such as being part of a FRAMESET), it is recommended to use the SAMEORIGIN directive. However, if you do not expect the page to be framed, the DENY directive should be used. Another option to consider is implementing the “frame-ancestors” directive available in the Content Security Policy (CSP).
By appropriately configuring these headers or directives, you can control how your web pages are framed, ensuring enhanced security, and preventing potential clickjacking or framing attacks.
| Severity | Name |
|---|---|
| MEDIUM | Absence of Anti-CSRF Tokens |
The absence of Anti-CSRF tokens in an HTML form exposes it to CSRF attacks, where attackers trick users into unknowingly sending requests to perform actions on their behalf. These attacks exploit predictable URL/form actions and exploit the trust between users and websites. CSRF attacks can be effective in various scenarios, including active user sessions, HTTP authentication, and local network proximity. Recent techniques even enable information disclosure. The risk increases if the target site is vulnerable to XSS attacks, as XSS can facilitate CSRF within the same-origin policy.
To protect against Cross-Site Request Forgery (CSRF) attacks, consider implementing the following security measures:
- Include anti-CSRF tokens in the company’s web application forms. These tokens should be unique for each user session and included in all requests that modify server-side state. Verify the token’s validity on the server-side before processing the request.
- Set the SameSite Cookie attribute on your cookies to restrict their usage to the same site. This prevents the browser from sending cookies in cross-site requests, mitigating the risk of CSRF attacks.
- Validate the HTTP Referer header to ensure that requests originate from the same site. However, be aware that this method can be circumvented or unreliable in certain scenarios.
- Use CSRF Protection Libraries such as OWASP CSRFGuard, Django’s CSRF protection, or Spring Security’s CSRF protection.
- Implement a Content Security Policy to control which external resources can be loaded by your web application. This can help prevent malicious code injection and mitigate CSRF risks.
- Finally, one of the most important security measures is to educate the collaborators. Inform them about the risks of CSRF attacks and encourage them to exercise caution when clicking on unfamiliar links or submitting forms.
| Severity | Name |
|---|---|
| MEDIUM | Location of the web server |
Based on our understanding, most ABC’s clients are from Portugal. However, during the footprinting process, it was discovered that the webserver is located in the USA. This raises an important question regarding server location. Ideally, the server should be situated in Portugal to ensure the lowest possible latency for the clients.
Internal network analysis
The process of performing a network analysis is a complex process because it can be done in multiple ways. Scanning is one of them and it consists of identified devices in the network including their IP addresses, operating systems, and other information. Sniffing is the active process that makes use of certain attacks to try to redirect and intercept the traffic accessing sensible data.
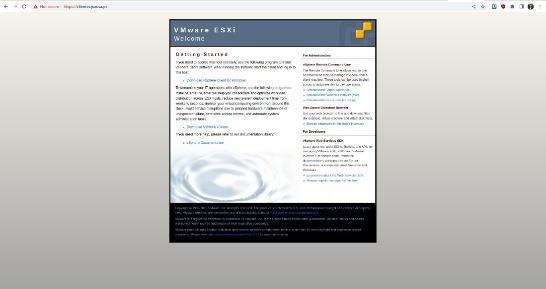
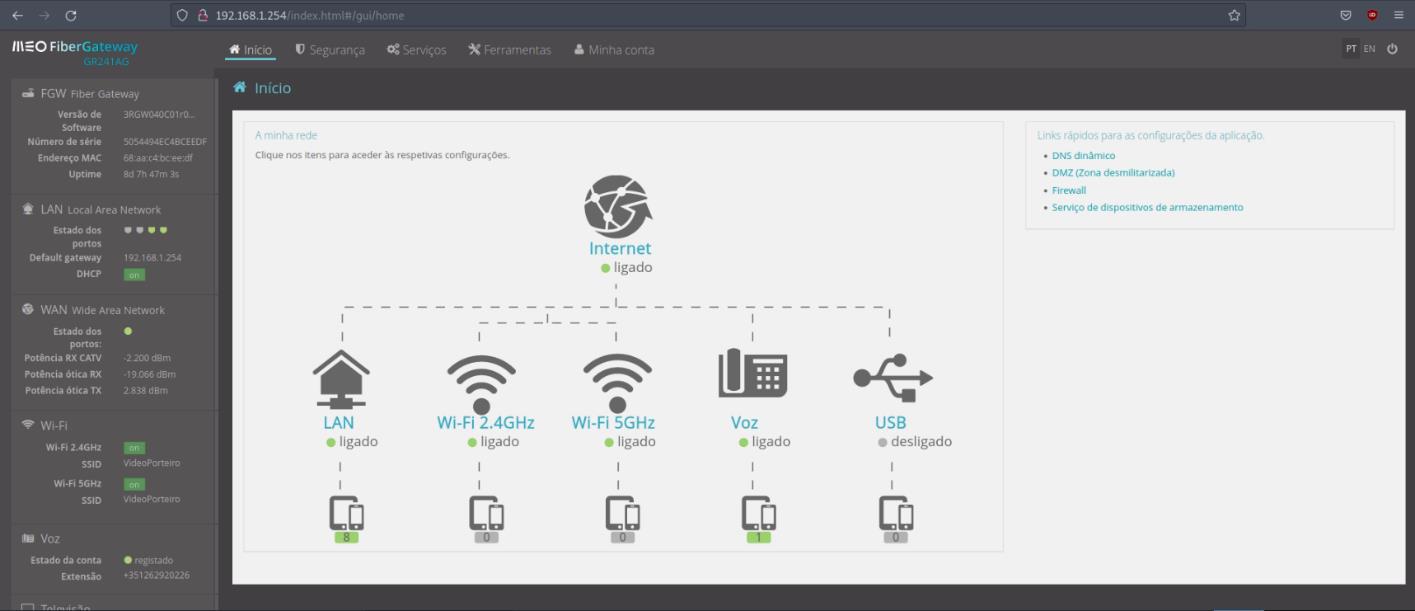
After the footprinting we found that the domain clientes.ABC.pt is pointing to a different server, this one is pointing to a server in Portugal and this server is VMware ESXI server running instances of TrueNAS on port 6080, unify controller on 8443 and pfSense on 7443.
| Severity | Name | Target |
|---|---|---|
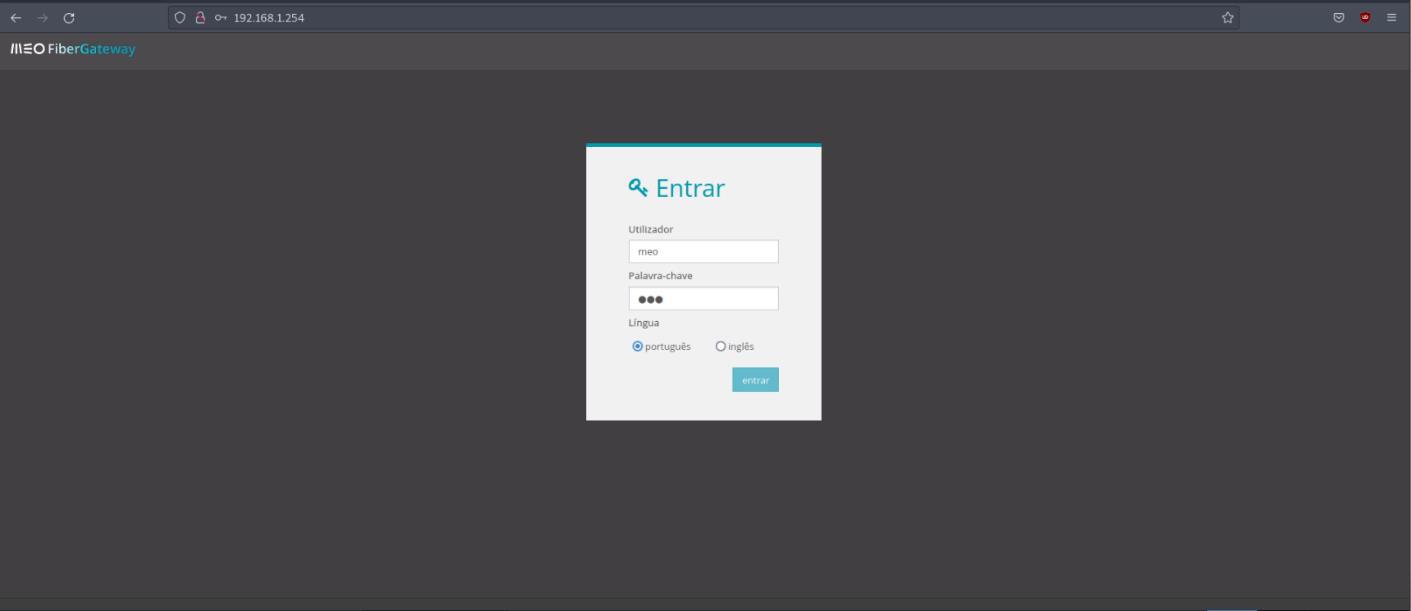
| CRITICAL | Default Credentials | Router – 192.168.1.254 |
The main router of the company currently utilizes default credentials (m-m) to access the router admin page. This represents a CRITICAL risk to the organization’s network infrastructure, as it allows anyone within the network to gain access to the router page. The implications of such unrestricted access are potentially catastrophic, as it enables unauthorized individuals to engage in malicious activities, including injecting custom firmware onto the router and obtaining passwords for the networks.
To mitigate this significant security vulnerability, it is imperative that the default password for the router’s admin page be changed immediately. By implementing a unique, strong, and confidential password, the organization can effectively restrict unauthorized access and safeguard the network infrastructure from potential breaches.
| Severity | Name | Target |
|---|---|---|
| CRITICAL | Common password | Wi-Fi network - ABC |
A network with a commonly used password on a 2.4GHz network is a severe security risk. It makes it easier for intruders to gain unauthorized access to the Wi-Fi network, it can grant them entry to the router’s configuration page due to default credentials. This opens the possibility of malicious activities such as injecting custom firmware, altering network settings, changing to a potentially vulnerable custom firmware, or even completely shutting down the network.
| Severity | Name | Target |
|---|---|---|
| MEDIUM | Unencrypted Telnet Server | Router – 192.168.1. |
The company’s router has a Telnet server configured to operate over an insecure channel. This method of using Telnet places a serious security risk on the business. Plain text transmission makes sensitive information, like usernames, passwords, and commands, vulnerable to interception by unauthorized parties. This creates a vulnerability where a malicious attacker, positioned in the middle of the communication, could eavesdrop on the Telnet session. As a result, they could gain access to sensitive company data or even manipulate the traffic exchanged between the router and other devices.
We advise turning off the telnet server if the company isn’t using it at the moment. However, it is strongly encouraged to switch the company’s router from Telnet to SSH (Secure Shell) if the server is used. SSH offers an encrypted and secure connection, protecting the company’s login information from being intercepted.
| Severity | Name | Target |
|---|---|---|
| MEDIUM | Samba Badlock Vulnerability | Router – 192.168.1.254 |
The router currently in use has been identified to have a medium security vulnerability known as the Samba Badlock Vulnerability. This vulnerability affects the Samba software suite, which provides file and print services for Windows clients. Samba Badlock exploitation can result in denial-of-service attacks, arbitrary code execution, and unauthorized access.
We do not recommend using the currently installed Samba version. We further encourage upgrading the Samba software to version 4.2.11 / 4.3.8 / 4.4.2 or later.
| Severity | Name | Target |
|---|---|---|
| MEDIUM | Cleartext Transmission of Sensitive Information via HTTP | Gigaset DX800A administration portal – 192.168.1.15 |
The telephone administration portal transmits sensitive information in cleartext via HTTP. An attacker exploiting this situation could compromise or eavesdrop on HTTP communication, utilizing a man-in-the- middle attack to gain access to sensitive data such as the security pin in this case.
To enhance security, the company should enforce the use of encrypted SSL/TLS connections for transmitting sensitive data. Moreover, ensure that the host/application redirects all users to the secure SSL/TLS connection before allowing input of sensitive data into the portal.
| Severity | Name | Target |
|---|---|---|
| MEDIUM | FTP Unencrypted Cleartext Login | QNAP – 192.168.1.2 |
QNAP – 192.168.1. 2
The FTP Unencrypted Cleartext Login vulnerability refers to the use of unencrypted communication for authentication and data transfer over the File Transfer Protocol (FTP). In this case, the vulnerability has been identified on the QNAP device with the IP address 192.168.1.2.
The FTP protocol is frequently employed for file transfers between systems. FTP, however, presents a serious security concern when used without encryption. Usernames, passwords, and data are sent in plain text over an unencrypted FTP connection, making it possible for anyone with access to the network to intercept and read private information.
We recommend enabling FTP over SSL (FTPS) for secure file transfer. FTPS is an extension of the traditional FTP that adds an extra layer of security by incorporating SSL/TLS encryption protocols.
| Severity | Name | Target |
|---|---|---|
| MEDIUM | AppleShare IP / Apple Filing Protocol (AFP) Unencrypted Cleartext Login | QNAP – 192.168.1.2 |
QNAP – 192.168.1. 2
The AppleShare IP / Apple Filing Protocol (AFP) is commonly used for communication between Apple devices and the QNAP device. However, it is important to note that the AFP Unencrypted Cleartext Login vulnerability poses a security risk due to the transmission of sensitive information in plain text.
To ensure the confidentiality and integrity of the data exchanged between Apple devices and the QNAP device, the company should implement secure communication measures, such as enabling AFP over TLS/SSL or utilizing a VPN for secure access.
Wi-Fi Analysis
During the Wi-Fi analysis test, we found out that only one network (ABC) is being used. Therefore, the insecure network “ABC” can be disabled.
The Wi-Fi network that is used by the workers has the same password as the phone number of the company plus one “0” character.
| Severity | Name | Target |
|---|---|---|
| HIGH | Unsecure Wifi Password | ABC main wifi network |
This allows people from outside of the company to easily predict the Wi-Fi password of the network where all the workers are connected. Since the password is just numbers a user can simply capture the handshake and in a matter of hours brute forces the password. We also spoke to one of the workers that told us that this password has been the same for 20 years.
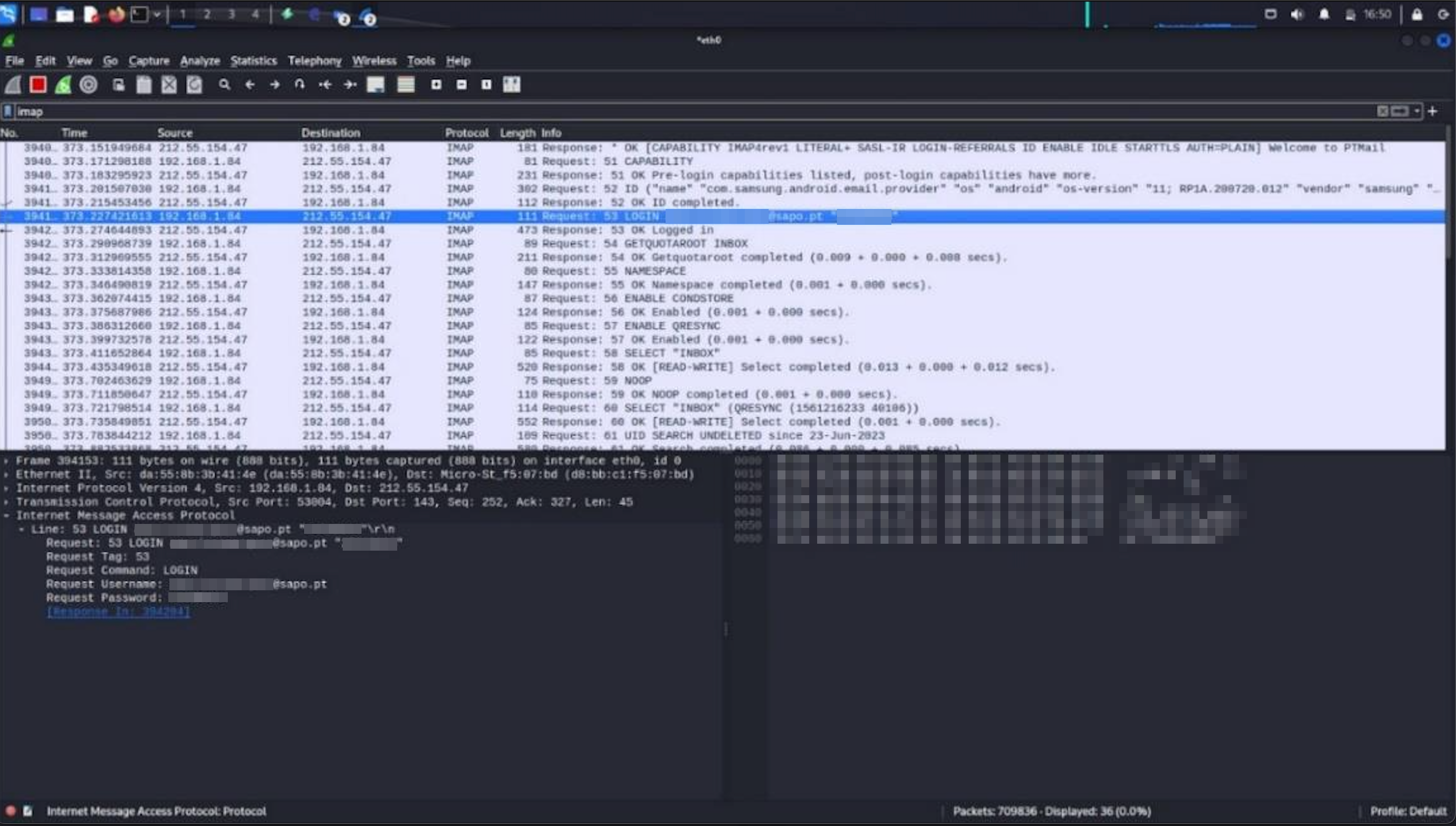
Sniffing
While we were sniffing, we found an unsafe login attempt to an email client executed by a company’s worker. We tried the credentials {username: americosmarques@sapo.pt, password: 25 **} and we
figured out that the email had two factor authentication enabled. However, he strongly recommends stopping using the application that has this vulnerability.
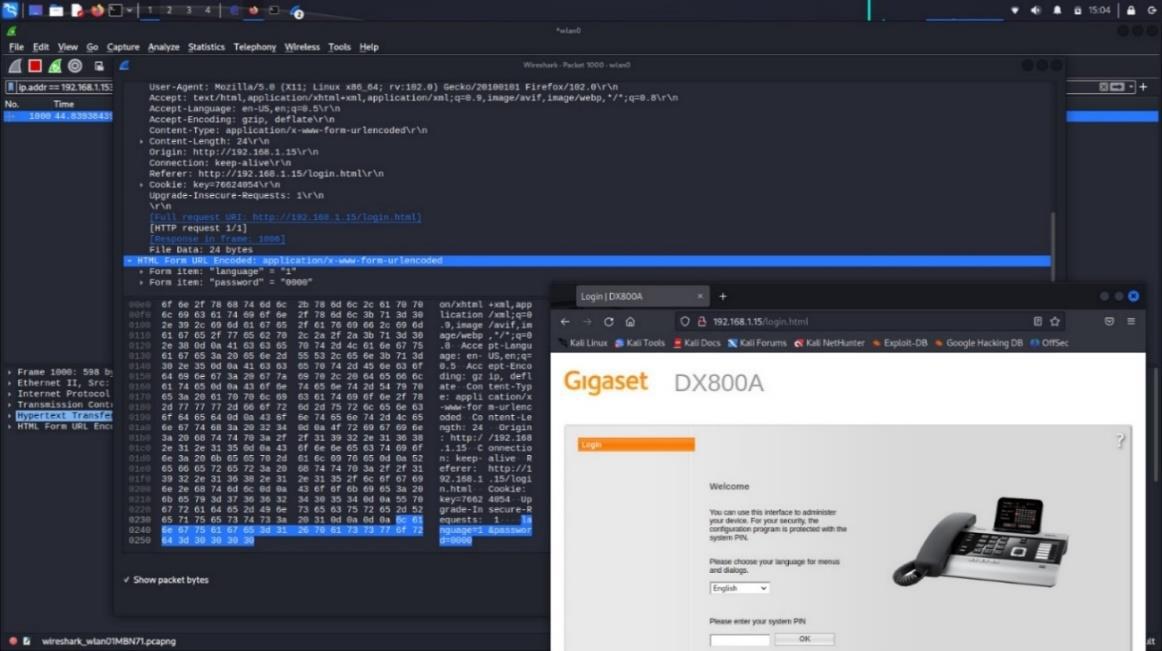
After the discovery of the IP of the administration panel of the phone call server. Furthermore, we also employed a tool to test multiple common passwords. We easily got a simple pin, “0000” that got us in the control panel of the Phone call server. As can be seen in the picture above, the website communicates through HTTP we could easily sniff and intercept any traffic between anyone and the phone call server, including the security pin in plain text.
| Severity | Name | Target |
|---|---|---|
| MEDIUM | Simple password | Phone administration panel |
QNAP NAS vulnerabilities assessment
After conducting a network analysis, we identified several insecure protocols, including FTP, with open ports on the QNAP NAS. Our objective in this phase was to determine if any communications were taking place through these protocols. Given that all computers within the company operate on the Windows operating system, communication with the NAS exclusively utilized the SMB protocol, specifically SMB2, which is considered secure.
During our investigation, we tested two different exploits. The first exploit we attempted is known as the “overkill exploit” targeting a vulnerability that was likely patched in November 2020 and April 2021. This exploit involves DNS spoofing, where we redirected “update.qnap.com” to our machine. Subsequently, the exploit sends HTTP GET requests to “/cgi-bin/qnapmsg.cgi?lang=xxx”, causing unpatched QNAP devices to download an XML file from “update.qnap.com” via insecure HTTP. We could then respond with a modified XML file, which, upon parsing by the QNAP, would trigger a system call resulting in a reverse shell. Unfortunately, our attempt to exploit this vulnerability was unsuccessful, leading us to conclude that the QNAP NAS is updated and secure.
The second exploit we explored is called the QNAP Pre-Auth Root RCE (CVE- 2019 - 7192 ~ CVE- 2019 - 7195) Exploit, which enables the reading of system files, including the shadow file containing passwords. However, this exploit also proved unsuccessful in our testing.
Based on our findings, we can affirm that the QNAP NAS does not exhibit any major vulnerabilities. Consequently, we recommend closing the FTP port, as it is not utilized.
Consider migrating from Openvpn UDP to Wireguard
| Severity | Name | Target |
|---|---|---|
| LOW | VPN protocol change | VPN server |
ABC has another office in another location and the workers there access the QNAP via OpenVPN using the UDP protocol. We suggest changing to Wireguard because it has less overhead in comparison to OpenVPN and overall, it would improve the bandwidth and throughroughput by up to 30%.
Conclusion
In conclusion, the penetration test conducted on the ABC company successfully met its goals, as several vulnerabilities were identified and brought to light, enabling the organization to take necessary measures to enhance their security posture and protect their assets. This project was a transforming journey that has not only broadened our knowledge but also deepened our understanding and sharpened our talents in the complex topic of cybersecurity.